A hierarchical deterministic wallet (or “HD Wallet”) is a wallet in which all of its keys and addresses are generated from a single source. The best part about these wallets is that you can generate new public keys without knowing the corresponding private keys.
HD Wallet uses
- Single Backup
Each time you wanted to receive bitcoin, you would generate separate pairs of private and public keys in a basic wallet. This works fine, but it requires you to back up your wallet every time you receive a new payment.

A hierarchical deterministic wallet, on the other hand, can use a single seed to generate a master private key, which can then be used to generate billions of “child” private keys and public keys. All you need to back up now is the seed because the master private key you generate from it will always generate keys for your wallet in the same way (deterministically).

- Organization
Each child key in the wallet can generate its own keys, allowing you to organize the keys in your wallet using a tree structure (or hierarchy). For instance, different parts of the tree could be used for different “accounts.”

- Generating public keys independently
A master private key has a corresponding master public key, which can generate the same child public keys without knowing the private keys. As a result, you could send the master public key to a different computer (for example, a webshop server) to generate new receiving addresses without fear of the private keys being stolen if the server is hacked.
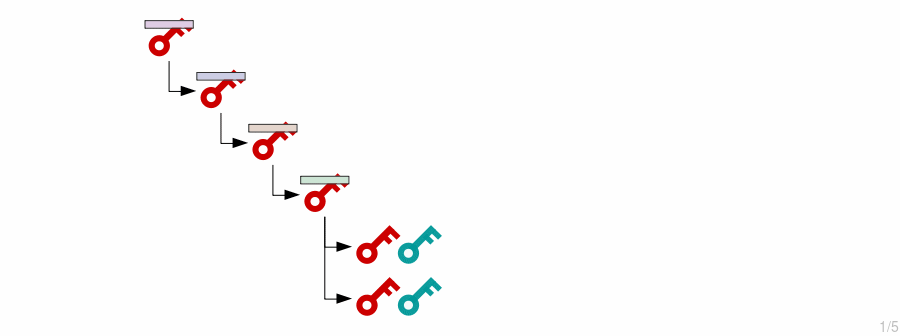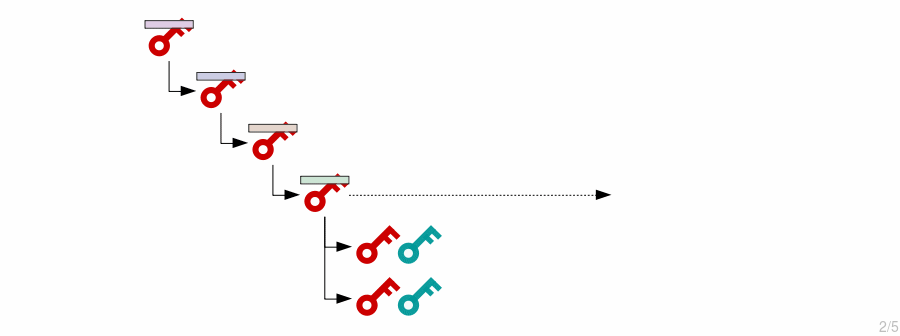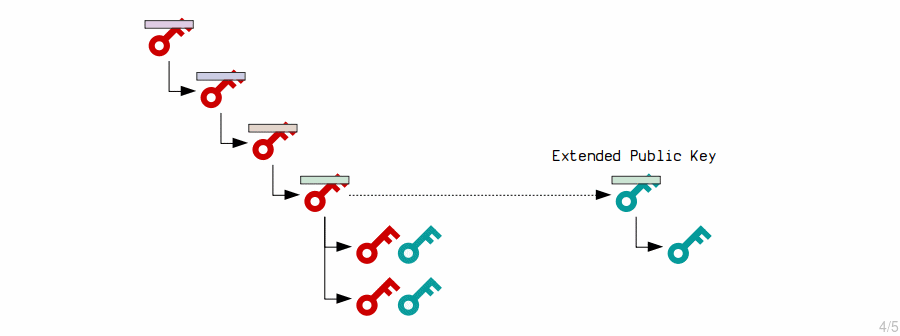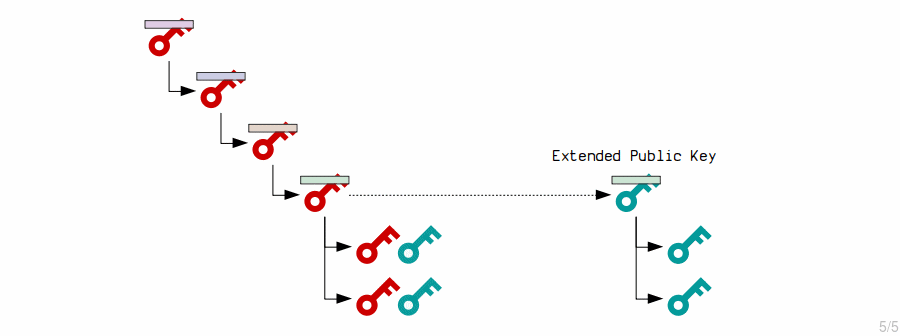
This is useful for hardware wallets, where you want to keep your private keys on a secure device but also want to be able to generate new addresses on a different computer to receive payments.
HD Wallets Working
- Seed
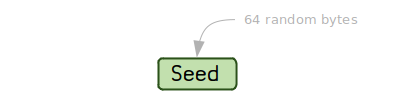
To begin an HD wallet, you must generate 64 random bytes, which will serve as our seed.
seed: b1680c7a6ea6ed5ac9bf3bc3b43869a4c77098e60195bae51a94159333820e125c3409b8c8d74b4489f28ce71b06799b1126c1d9620767c2dadf642cf787cf36
- Master Private Key
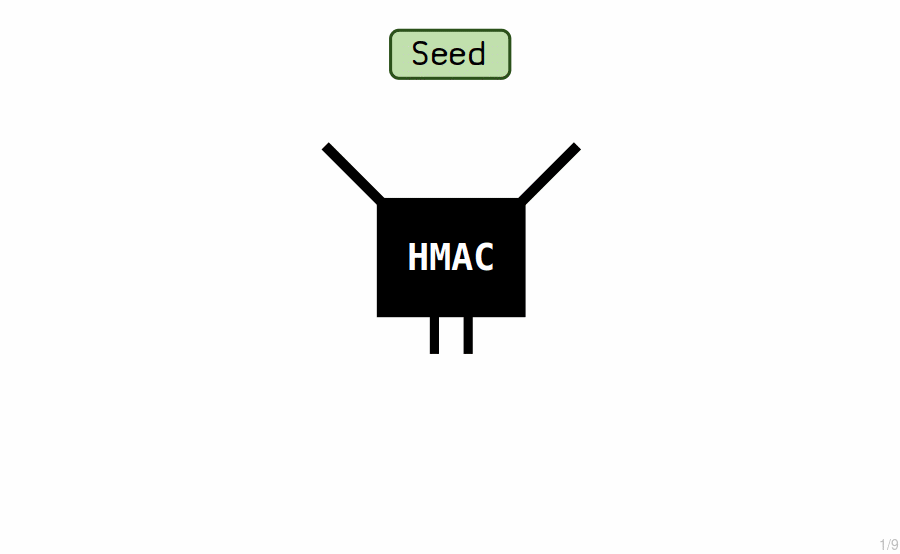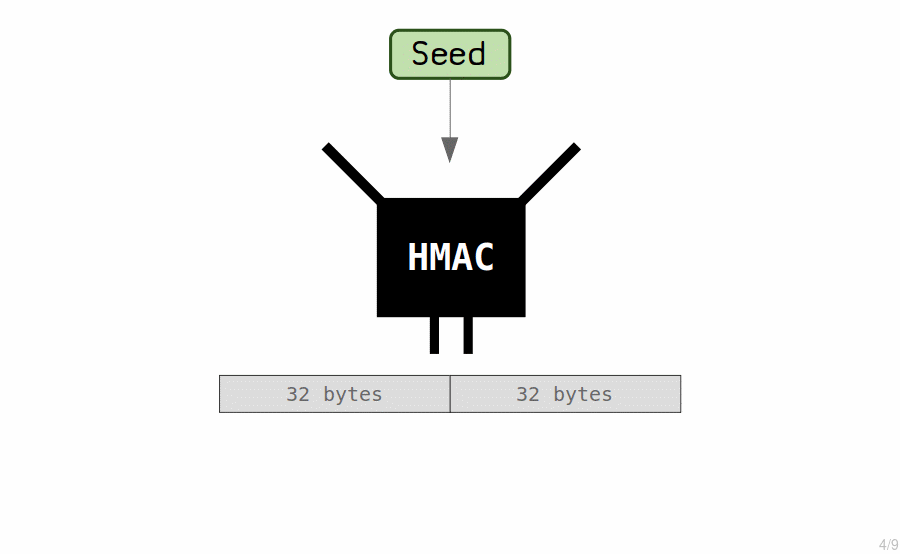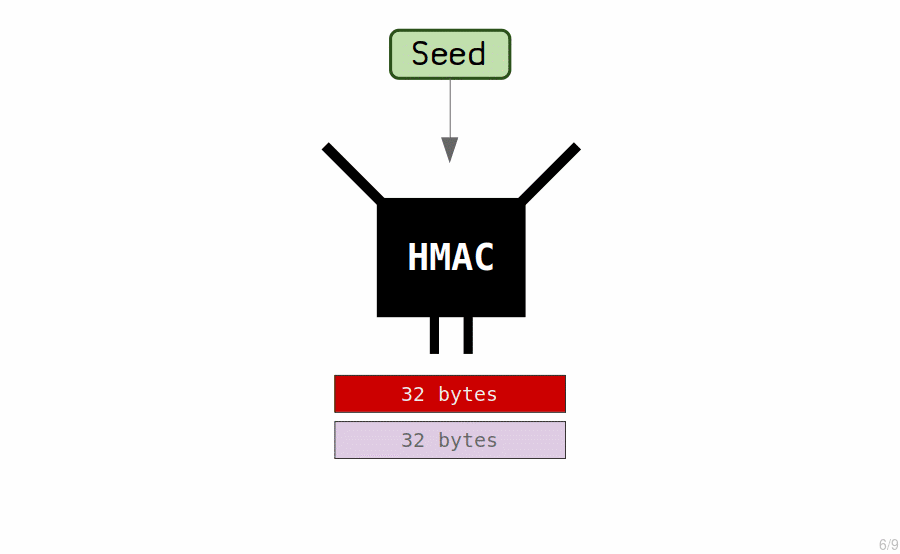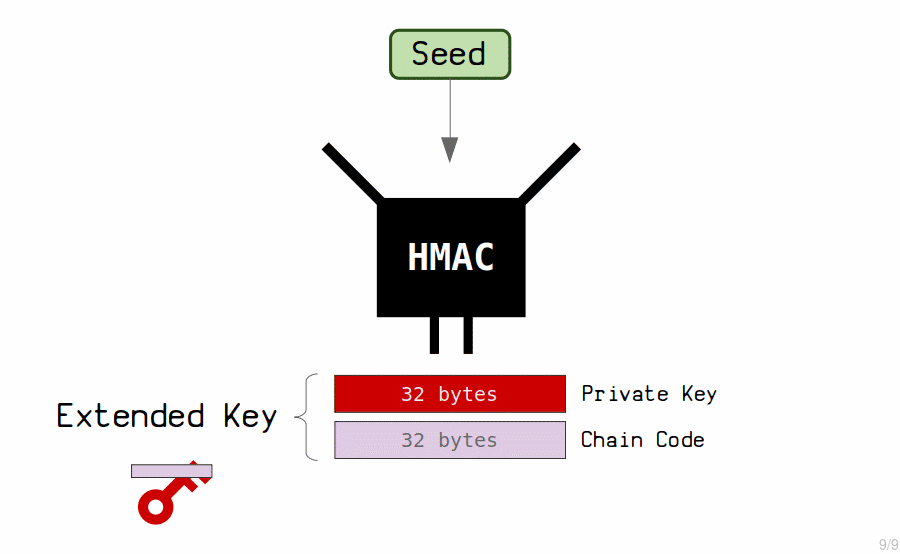
The “master key” is generated by running the seed through a hash function (known as an HMAC) to generate another set of 64 bytes.
These 64 bytes are used to generate our master extended private key.
The private key is the first 32 bytes.
The chain code is the last 32 bytes.
The chain code is simply an extra 32 bytes that we combine with the private key to form what is known as an extended key.
Why are we hashing the seed? We could generate the master extended private key directly from the 64-byte seed. However, future child extended keys will be generated using the HMAC, so we should be consistent in how we generate both.
Extended Private Key
seed: d21c4706c010823505f09c0c51c5dceacfd466fb56da019f3e3a148028300945db382784c147aea03e6866f8bc5adbffe2bf8552d72001f4141440b19f400729 master extended private key: private key: 23a19e4d7813660525ba64d32a2b754c2e47af788b04867782736d36d2fe314f chain code: 3139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e6164660
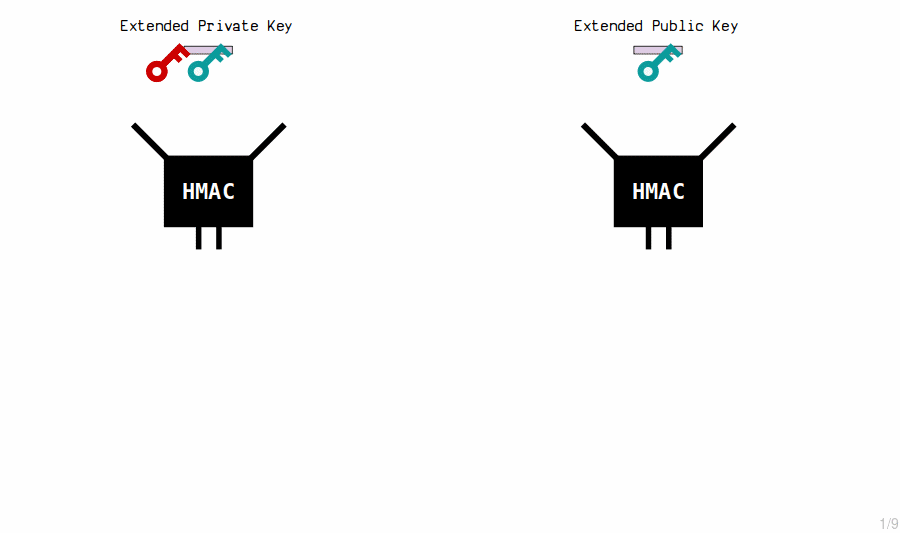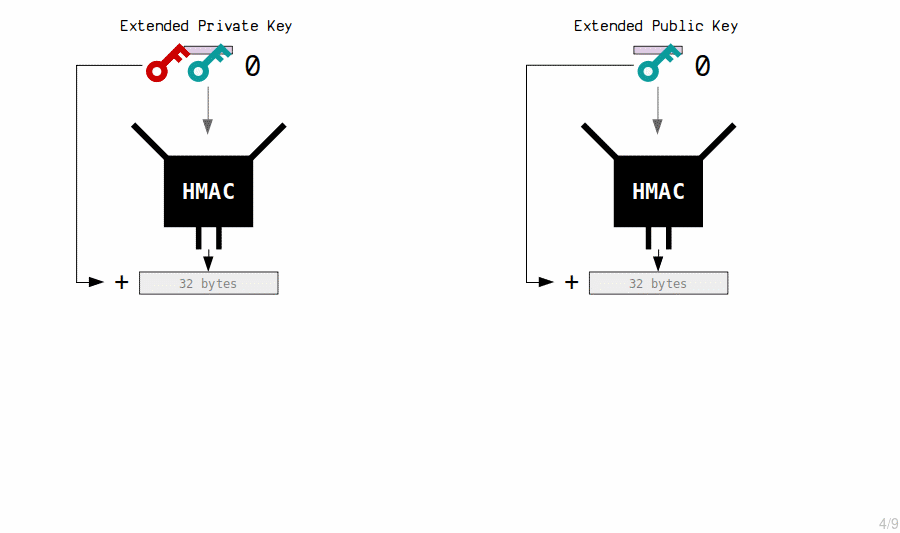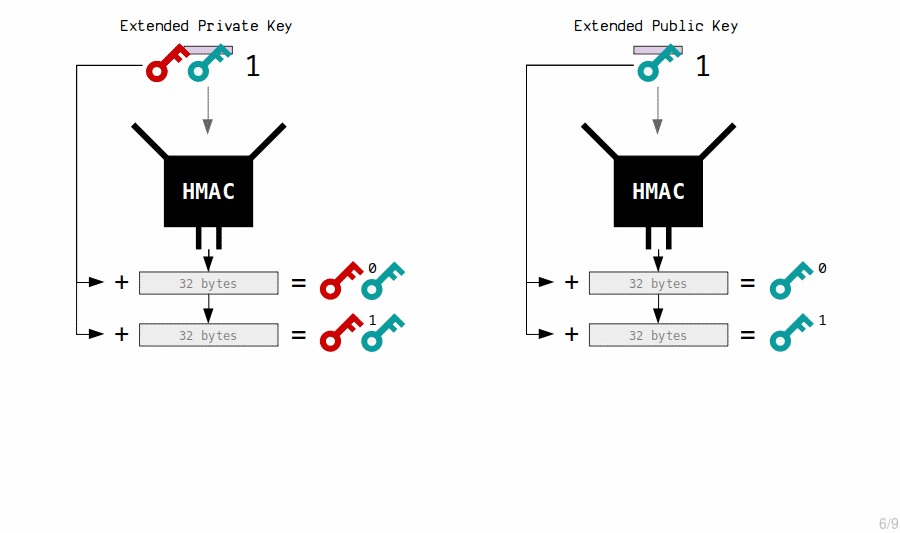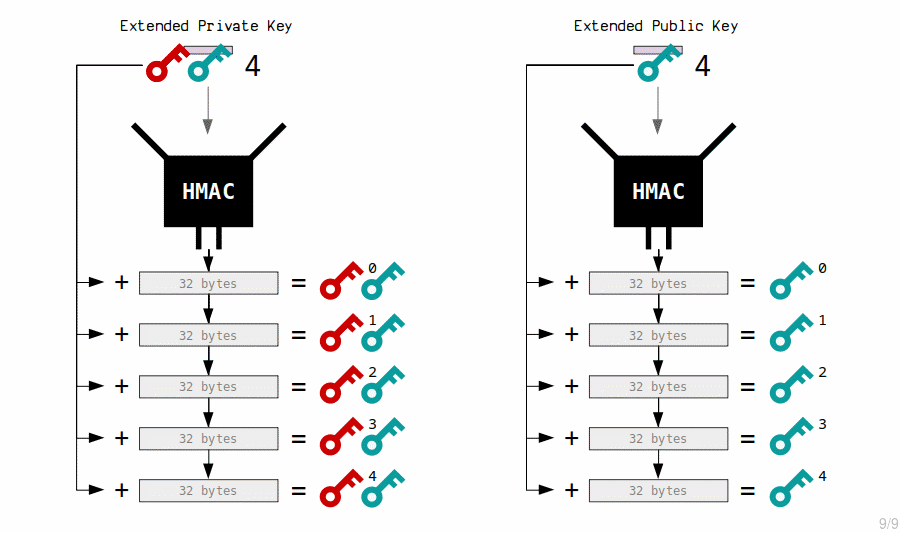
- Child Keys (Basic)
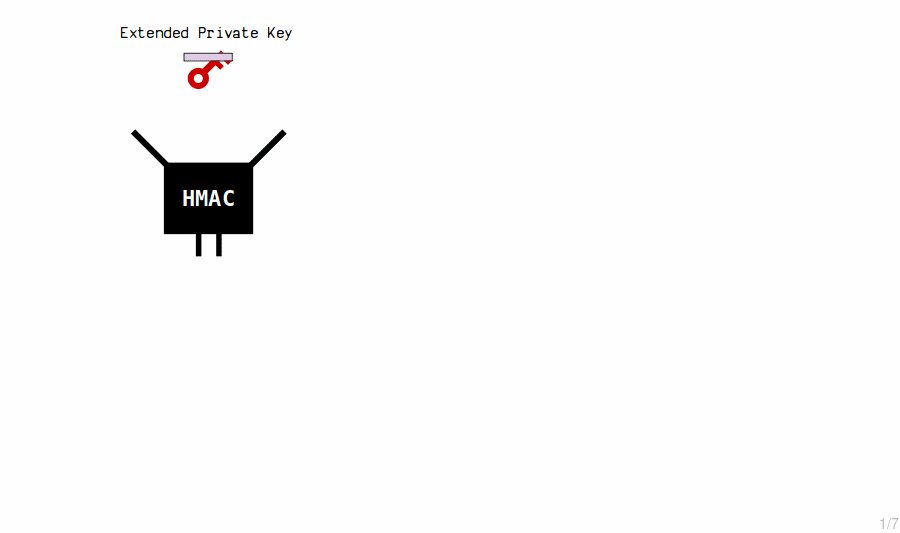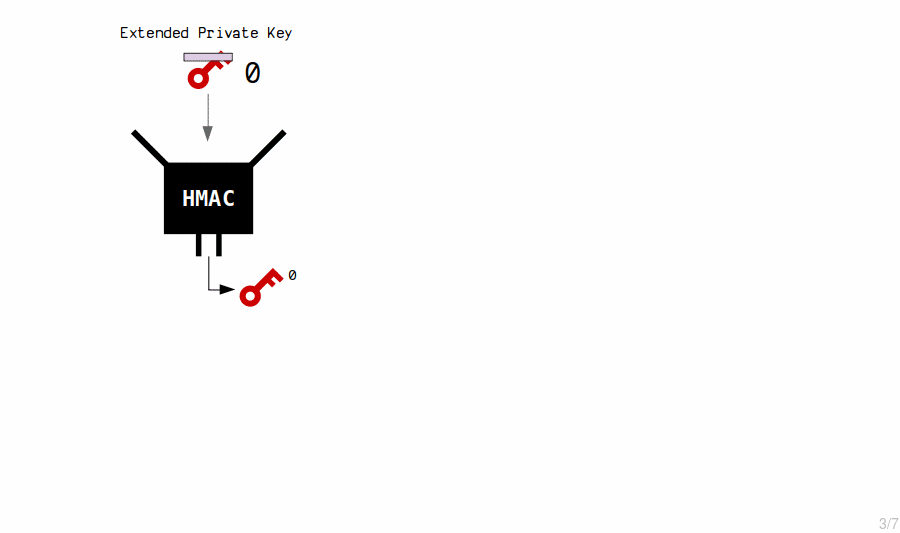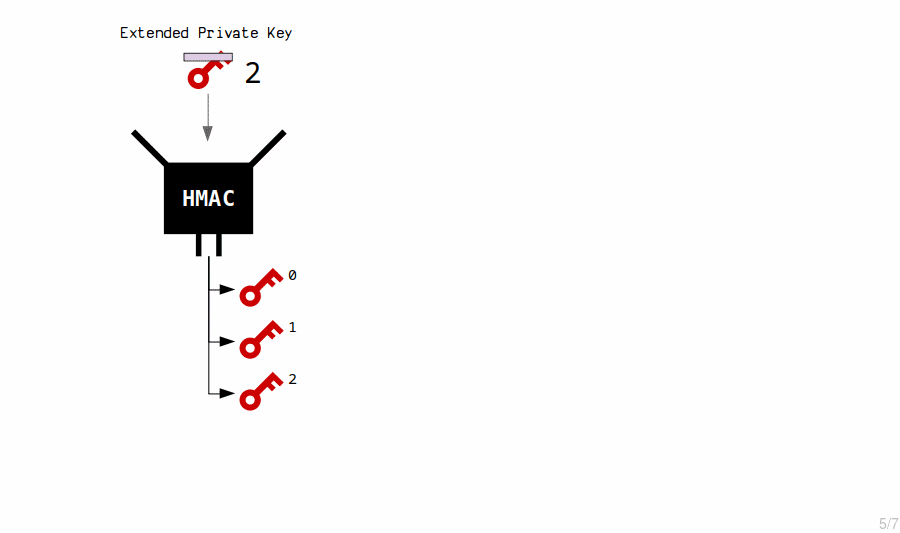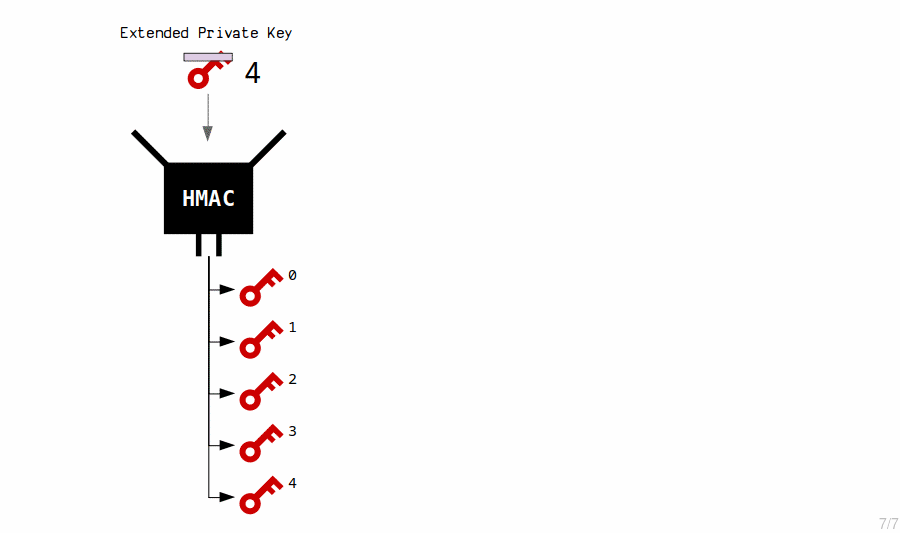
The HMAC function is used to generate new child private keys from an extended private key’s contents (private key and chain code). Each time, we also include an index number, which allows us to generate multiple child keys from a single master key.
By changing the index, the hash function produces a completely different result.
seed: d21c4706c010823505f09c0c51c5dceacfd466fb56da019f3e3a148028300945db382784c147aea03e6866f8bc5adbffe2bf8552d72001f4141440b19f400729 master extended private key: private key: 23a19e4d7813660525ba64d32a2b754c2e47af788b04867782736d36d2fe314f chain code: 3139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e6164660 child 0: private key: 6ba2c281775154bbe0c00cdd977ec2982cb6a16471b6a1bd0d2d0e80ffd18fe0 public key: 03e363156bceb483139dab5db66ae074e4b789bb0571cecbbee2c53209fb9dd92c child 1: private key: 3d99c8e35ffae9d9a9f42a9226f201fb23205a36063eba8c4a8019267a581e27 public key: 022f524c7cf0d3b6c87dc980806f1575a882561bde9ae47546ee437eb5775e1547 child 2: private key: 4375883b170249ee15cbacd0993d092af8a7483dbe739ea5ac24dd4caf422d55 public key: 02a7546067a46bca643a8afa34d2278140228fe11d0560a098bb82ab2786b884fe
Thus, new private keys are created by hashing the master extended private key with an index number.
An extended key can generate 2,147,483,648 of these children.
- Child Keys (Advanced)
What if we want an extended private key that can generate child private keys and public keys, as well as an extended public key that can generate the same child public keys?
Extended Public Key
First and foremost, we must create the extended public key. This is simply the public key from the extended private key with the same chain code:

seed: d21c4706c010823505f09c0c51c5dceacfd466fb56da019f3e3a148028300945db382784c147aea03e6866f8bc5adbffe2bf8552d72001f4141440b19f400729 master extended private key: private key: 23a19e4d7813660525ba64d32a2b754c2e47af788b04867782736d36d2fe314f chain code: 3139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e6164660 master extended public key: public key: 036798c06d21b75950e62236cf81d70571f554d582820277192b1a74263ac19109 chain code: 3139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e6164660
Extended Private Key Children
The master extended private key generates child private keys by processing the contents of its corresponding extended public key with the HMAC function and appending the result to the original private key.

seed: d21c4706c010823505f09c0c51c5dceacfd466fb56da019f3e3a148028300945db382784c147aea03e6866f8bc5adbffe2bf8552d72001f4141440b19f400729 master extended private key: private key: 23a19e4d7813660525ba64d32a2b754c2e47af788b04867782736d36d2fe314f public key: 036798c06d21b75950e62236cf81d70571f554d582820277192b1a74263ac19109 chain code: 3139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e6164660 child 0: private key: 64aeac0a1fc22c8f65ff273dd61d56c1b24854bd4d8a56c8c3e2a9182ffdfe19 public key: 02e66cb395dd81e7aa183554ec10716ec56e74c77f9d65bff6b5e78a272ec4c26f child 1: private key: 249cfa2a232c88e63e4394176c4b3f9638c52c8591ff653b4fdffa11a16202fe public key: 02f17f1f04c5f5c92af0d4e09c9d47cc230be63de389beb78ce919aae0480b43e2 child 2: private key: daaa34c580fd22117685356cd2ab5a278ec80138e268538fc2ba2ed04932e3ed public key: 0288e6d81a1e0990924cd826d1a33099d5181022e264fe2d9f1ef79007d4c5858e
Extended Public Key Children
The master extended public key generates new child public keys by running their contents through the HMAC function and then appending the results to the original public keys.
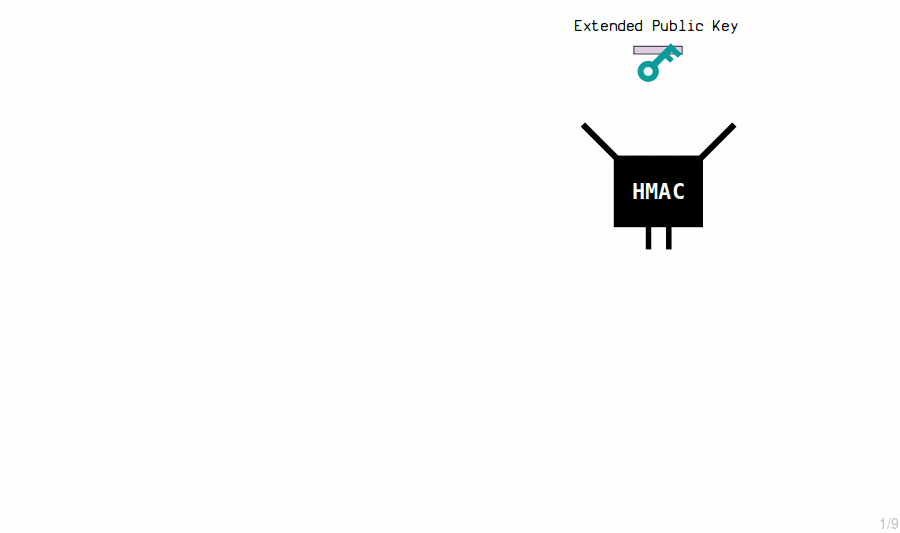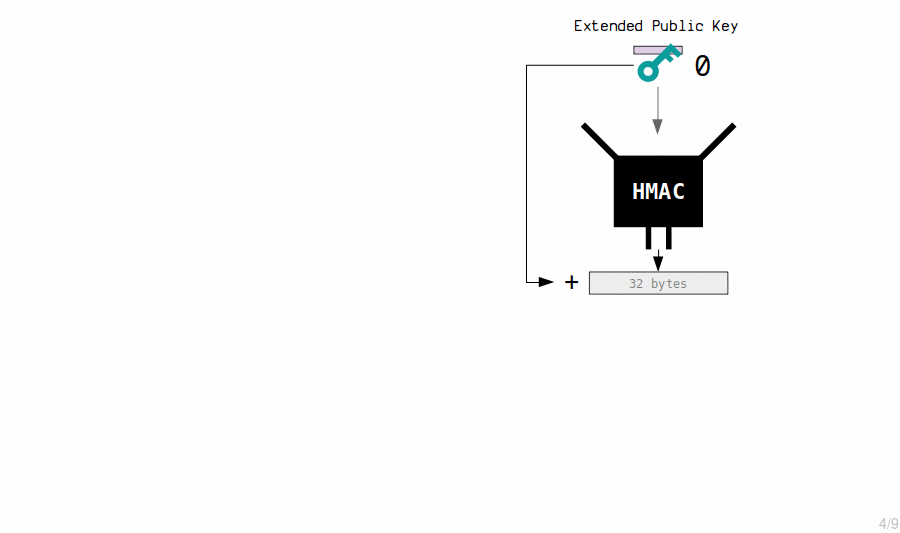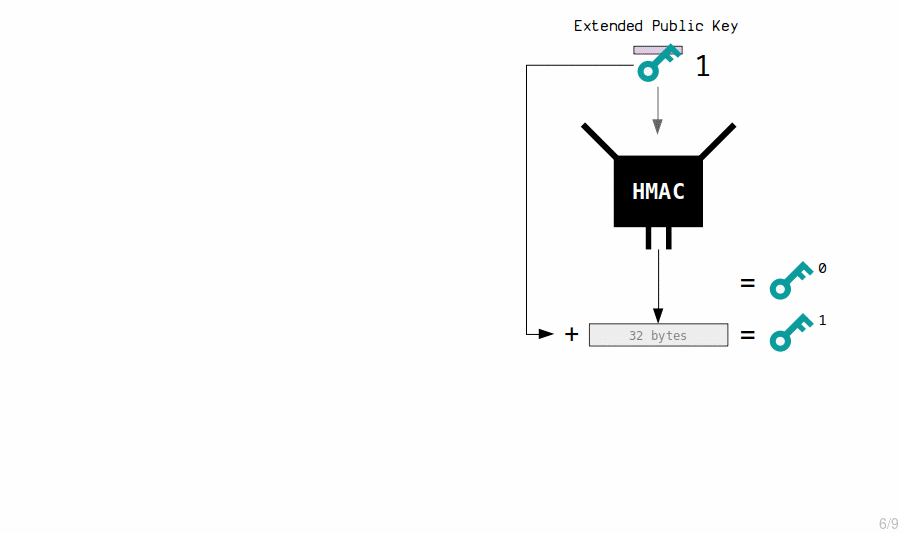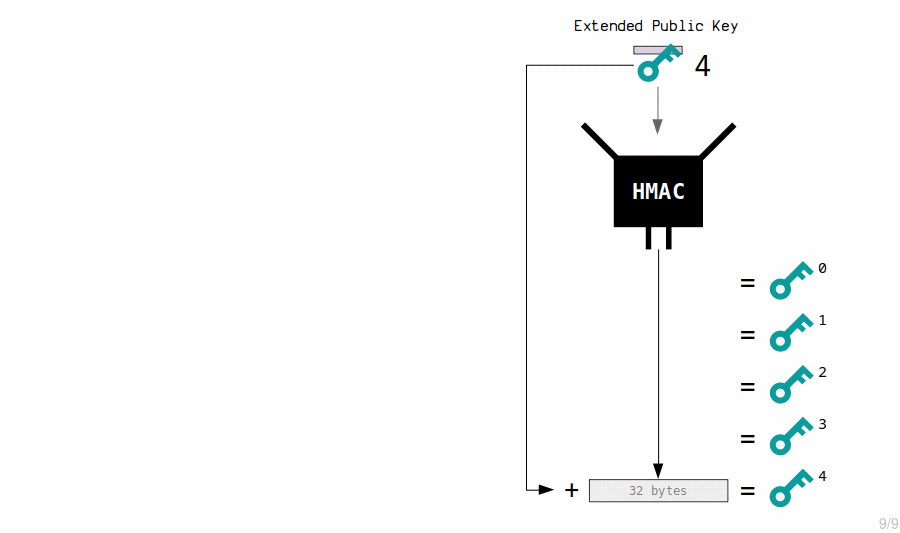
master extended public key: public key: 036798c06d21b75950e62236cf81d70571f554d582820277192b1a74263ac19109 chain code: 3139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e6164660 child 0: public key: 02e66cb395dd81e7aa183554ec10716ec56e74c77f9d65bff6b5e78a272ec4c26f child 1: public key: 02f17f1f04c5f5c92af0d4e09c9d47cc230be63de389beb78ce919aae0480b43e2 child 2: public key: 0288e6d81a1e0990924cd826d1a33099d5181022e264fe2d9f1ef79007d4c5858e
Because the original private and public keys were both adjusted by the same amount, the new child’s private and public keys correspond.
An extended key can generate 2,147,483,648 of these children.
As a result, an extended key can yield a total of 4,294,967,296 children (2,147,483,648 advanced and 2,147,483,648 basic).
The appearance of an extended key
We serialize extended keys along with some extra data to make them easier to pass around.
When serialized, our master extended private key, for example, looks like this:
version: 0488ade4 # puts "xprv" or "xpub" at the start after encoding to base58 depth: 00 # how deep we are in the key tree index: 00000000 # the index number fingerprint: 00000000 # this is from the hash of the parent key chain code: 3139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e6164660 key: 0023a19e4d7813660525ba64d32a2b754c2e47af788b04867782736d36d2fe314f # prepend 00 for private keys serialized: 0488ade40000000000000000003139577130a7151af8a282759e348e044808ba5fd145bd4a0e75f0e7e61646600023a19e4d7813660525ba64d32a2b754c2e47af788b04867782736d36d2fe314f
Then we can make it more convenient by converting it to base58 (including a checksum)
xprv9s21ZrQH143K2YnHTTJ6hU47aTaYJvmLAqTh8c3Jp3tBEWvnkwQnaD8jpUUEBjhXQEuCgxKyFQFZWDbPPWFbQVrsP4BXHMGonyzcHDF7o9SThis is a better format for our extended key. It’s easier to transfer files between computers and import them into wallets.
Few examples of HD Wallets
Since 2013, the majority of modern wallets have been hierarchical deterministic. Here are some well-known examples:
- Electrum
- Samourai
- Mycelium
- Trezor
- Ledger
When you create the wallet, they each give you a seed, which is then used to generate all of the keys and addresses for it.
Conclusion
A hierarchical deterministic wallet can be used to generate new private and public keys.
It is deterministic because all of the child keys are generated from a seed, in the same way, each time, and it is hierarchical because the keys can be organized in a tree structure (or hierarchy). Another advantage is that the public keys in the wallet can be derived without knowledge of the private keys.
If you want to learn more about HD wallets, here are some technical explanations:
Mnemonic Seed (Generating a user-friendly seed for your HD wallet.)
Extended keys (Creating a master extended key, and deriving children from it.)
Derivation Paths (Common hierarchies used by wallets for organizing keys.)













