In this article, we discuss how two-factor authentication has been evolved to address the shortcoming of single authentication systems. We also discuss how we can utilize a blockchain technology to transform 2FA by migrating the centralized network into a decentralized blockchain network. As more Internet-of-Things devices require authentication credentials and users increase their repository of usernames and passwords for accessing web services, the emergence of 2FA solutions based on blockchain technology is inevitable.
Every organization has hundreds of applications and databases, and its employees access them every day using their credentials (that is, their username and password). An attacker with such valid credentials can bypass existing security solutions, as they look like a legitimate user. As per the Verizon Data Breach report in 2016, more than 63% of successful breaches involved compromised credentials. Two-factor authentication (2FA) provides an added layer to the existing credential-based system protection as a solution to this drastically growing problem. As such, in this article, we will cover the following two topics:
- What is 2FA?
- Blockchain for 2FA
1- What is 2FA?
With several data breach incidents, we’ve witnessed a massive increase in the number of social and professional website accounts being hacked. Sometimes, even a simple human error can cause huge trouble globally. Sometimes, it’s easy to predict the password of a user based on their daily activity, behavior, or even name. Users still tend to use plain text passwords to protect their account, and among the worst are password, 123456, and abcde.
2FA is an extra layer of security that’s used to ensure that only the legitimate owner can access their account. In this method, the user will first enter a combination of a username and password, and, instead of directly getting into their account, the user will be required to provide other information. This other piece of information can come in one of the following forms:
- Something that the user knows: This could be information such as a password, an answer to a secret question, or maybe a personal identification number (PIN).
- Something that the user has: This method includes the second level of authentication based on card details, through smartphones, other hardware, or a software token.
- Something that the user is: This is one the most effective ways to verify the user on the second step, and this is accomplished with biometric data such as keystroke dynamics and mouse behavior.
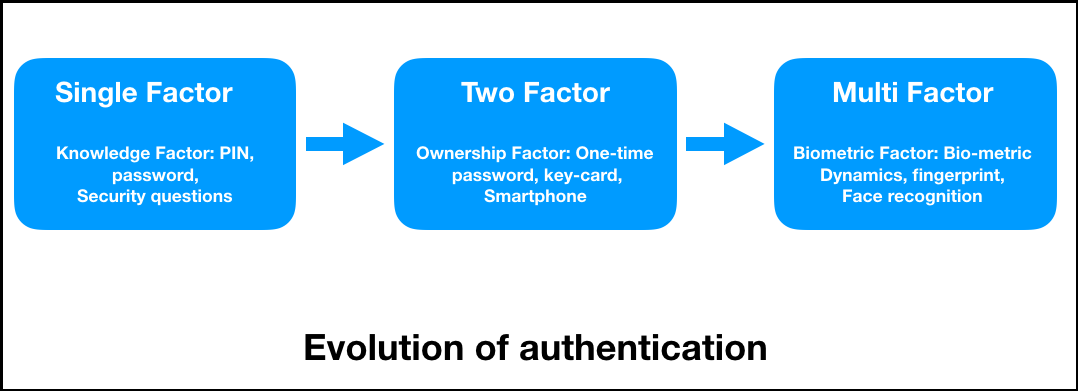
Evolution of user authentication
Organizations constantly struggle to find a better way to achieve more effective and reliable authentication systems. From the birth of the internet to the expansion of the public and hybrid clouds, authentication factors have been moving hand in hand. It is important to select a solution that supports robust authentication solutions. Organizations ensure that the system is future-proof and interoperable. The following diagram explains how the authentication system has evolved from single-factor authentication (SFA) to multi-factor authentication (MFA):
- SFA: It is based on the user’s pre-shared information: a PIN or a password, or, most likely, a security question. However, this is sometimes an issue, as a user may forget this pre-shared information if the user does not regularly access the application.
- 2FA: This is to overcome users’ tendency to forget pre-shared information based on what they know. It has methods such as smartphone, key card, or one-time password (OTP) verification. In this factor, the second step of authentication is dynamic in nature, and users don’t have to share anything with the application’s owner. This also avoids the risk of the account being compromised due to stolen credentials.
- MFA: This has several methods to authenticate users on the second level, such as voice biometrics, facial recognition, hand geometry, ocular-based methodology, fingerprint scanning, geographical location, thermal image recognition, and many more. However, this article is limited to only exploring 2FA.
The following diagram shows the evolution of authentication:
Why 2FA?
2FA helps both end user and business security, and there are several benefits of using it, which are as follows:
- Better security: By integrating a second level of authentication, SMS-based OTP reduces the risk of attackers impersonating legitimate users. This reduces the risk of account theft and data breaches. Even if the hacker gets the user’s credentials from the dark web, they won’t have the second piece of information required to completely authenticate.
- Increase in productivity: Mobile 2FA helps global businesses to use the second level of authentication seamlessly. Employees can securely access corporate applications, documents, and third-party systems from any device or location without sharing any confidential information.
- Reduction in fraud and increase in trust: Most fraud victims avoid going to certain retailers, even if the merchant wasn’t responsible for the data breach. 2FA builds a greater layer of trust with the user and also reduces fraud attempts on merchant sites.
How does it work?
2FA can be deployed in two modes: a cloud-based solution and an on-premises solution. We will understand both solutions and understand which fits better for what kind of deployment:
- Cloud-based solution: This is heavily used by e-commerce, online banking, and other online service-related web applications.
- On-premises solution: Organizations hesitate to allow cloud-based security solutions and tend to prefer on-premises solutions where an employee accessing web applications puts in a combination of a username and password. Now, this information goes to the internal VPN integrator, which handles credentials and exchanges a key between organizations and third-party 2FA providers. The third-party 2FA provider will generate the OTP and share this with the employee over SMS or through mobile applications. This model helps achieve privacy for an organization, as it doesn’t have to share the credentials with a third-party 2FA provider.
Challenges
In 2FA, the first level of authentication is a combination of a username and a password, but for the second level of authentication, this piece of information is provided from a central repository. This central repository is responsible for storing all information necessary to authenticate the user. Although 2FA increases the level of security with the second layer of authentication, it still encounters the drawback of having the centralized database store a list of secret user information. The central database can be tampered with or corrupted by targeted threats, and this can lead to massive data breaches.
2- Blockchain for 2FA
Blockchain is being hailed as one of the most revolutionary and disruptive technologies out there. Blockchain has been disrupting the cybersecurity solutions-based CIA security triad principle. 2FA has been critical in security measures for several years; however, attackers sometimes manage to compromise these systems. We will understand how blockchain can transform the 2FA system to achieve an improved security method.
How can blockchain transform 2FA?
By design, blockchain is a decentralized technology that allows transactions of any kind of value among multiple participants without the involvement of a third party. By leveraging blockchain, we can ensure that this sensitive information never remains on one database; instead, it can be within blockchain nodes that have immutability and can’t be modified or deleted. The following diagram shows a blockchain-based 2FA.
In this system, user devices will be authenticated by a third-party 2FA provider through the blockchain network. Each party in the blockchain network will hold the endpoint information securely and will activate the 2FA system to generate the second-level password.
This can either be deployed in the public domain, or even a private network with a third-party API call:
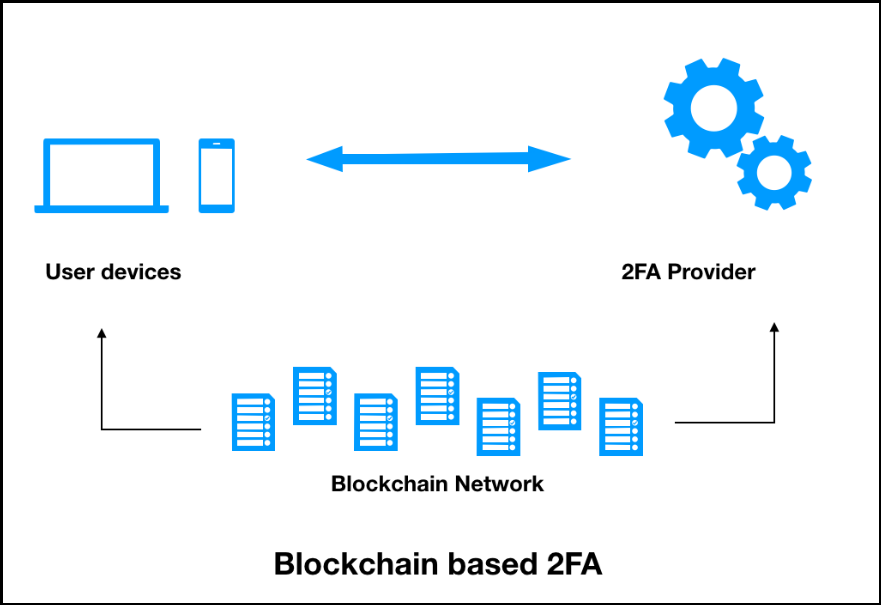
Solution architecture
Being the latest technology, blockchain is still in its testing phase with several organizations. For this article, we will be using the Ethereum blockchain to turn up the 2FA system. Ethereum allows an application to be programmed with a smart contract. In the following diagram, the basic flow between the user, the web application, and the Ethereum-based repository is depicted:
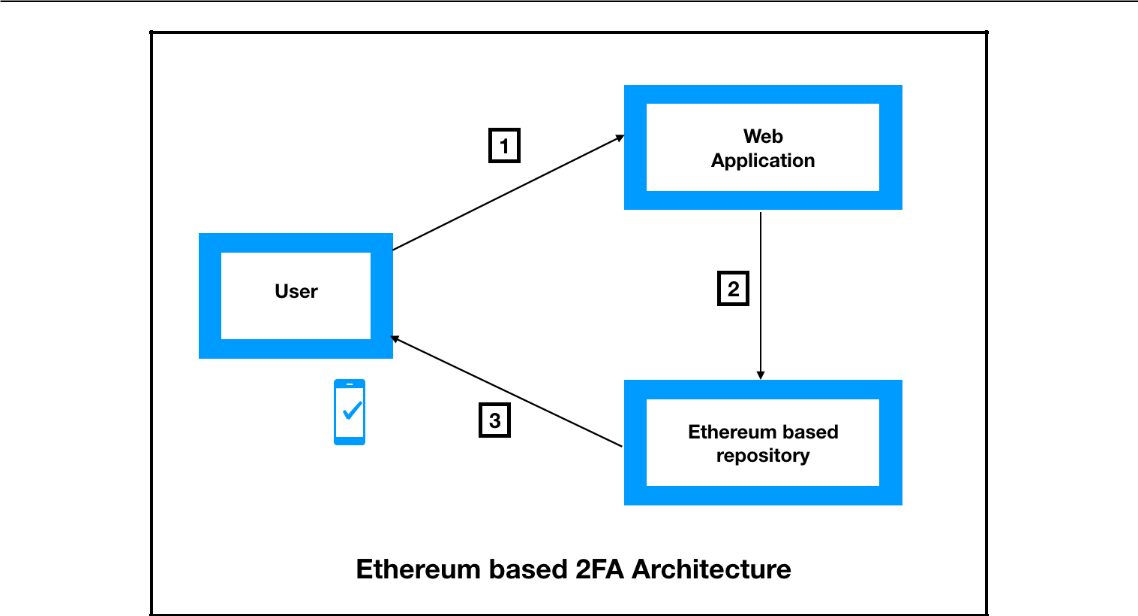
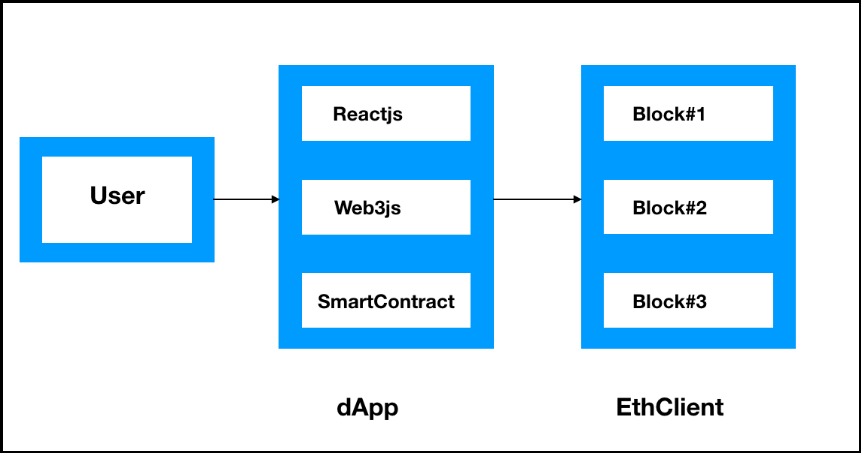
A user accesses the web portal and enters the first level of credentials. A web application will communicate to the Ethereum-based repository to generate the OTP and shares this with the user. Finally, the user enters the same OTP and gains access to the web application. Let’s gain some more insight into the Ethereum blockchain through the following diagram:
This article has been published from the source link without modifications to the text. Only the headline has been changed.