Bitcoin Introduction
The first (and arguably the most popular) blockchain is Bitcoin – the brainchild of the pseudonym Satoshi Nakamoto. The main motive behind Bitcoin was to serve as a decentralised and distributed global currency – without any centralised banks.
The ledger of transactions is stored as a chain (or a linked list) of blocks but the pointers con
necting these blocks are hash pointers which are dependent on the block information. The block information does not store the transaction directly. Each transaction becomes the leaf node of a Merkle tree, and the root of the Merkle tree is included in the block information. Therefore, any attempt to manipulate the data would not be possible without breaking (or forking) the chain. Also, as we are in distributed systems territory, we encounter one of the most famous problems of consensus, represented by the Byzantine General’s Problem. Essentially in a distributed system which is prone to Byzantine faults, how do we ensure that every node maintains the same ledger of transactions i.e. all the nodes are in consensus about the contents of the ledger? Bitcoin introduced an approach called proof of work (explained later in this section) to deal with it. However, other consensus algorithms like Proof of Stake and Proof of Burn, etc. are also used in other blockchains. Finding the answer to the cryptographic hash puzzle (proof of work for Bitcoin) is called mining. This is because whoever finds the answer gets a block reward in bitcoin (essentially creating or mining new bitcoin).
Bitcoin Features
The fundamental features on which Bitcoin (and other early blockchain platforms) was built upon
are –
- Distributed and Public – It is a distributed peer-to-peer (P2P) network hosted over the
internet. Anyone with an internet connection can join the network, view the blockchain or become a miner. - Decentralized – There is no central authority (like banks) in the network. This means that transactions cannot be reversed and there is little chance of grievance redressal.
- Consensus among nodes – All the nodes agree to the state of the blockchain. There might be temporary soft forks along the way but eventually only the longest chain survives.
- Cryptographically Secure and Immutable – The blocks are linked by hash pointers
which are computationally very expensive to find. Therefore blockchain contents are more or less immutable. The deeper the block is in the chain, the more difficult and resource intensive it becomes to manipulate transactions in that block. - Pseudo-anonymous – There are no unique identifiers on the blockchain. Everyone is known by their address. Also, there is no restriction on the number of accounts a person can have. This had earlier lead to Bitcoin becoming a hub for illegal activities as it provided people with ‘digital cash’.
- Easily Verifiable – Since the blockchain data is publicly visible and known to all, anyone
can view and verify transactions on the chain. - Limited Supply – The supply of bitcoins is limited to 21M. After this no new bitcoins can
be mined and miners will stop getting the block rewards and only receive the transaction fees.
Consensus Algorithms
The Consensus Problem occurs when different nodes in a distributed system need to come to an agreement in the presence of malicious nodes or faulty communication channels. [7] It is a very popular problem in distributed systems and Nakamoto gave an ingenious solution to it with proof of work. However, over the past decade different algorithms to solve this problem have come up with different blockchain platforms. Here we explain some of the popular consensus algorithms in use –
Proof of Work (PoW)
This approach was introduced in Bitcoin. Essentially, the miner (the person doing the work) has to find a value (also known as the nonce) which after being concatenated with the block contents and taking the hash gives a value which starts with a fixed number of zeroes (also known as the difficulty). The solution to finding this value is brute-force which is computationally very expensive. Therefore if anyone has to change the blockchain contents, he/she has to calculate the nonce value for that block and all the blocks after it up to the current block. This is highly infeasible. Since the work requires high computational power, the nodes with higher computational power become the miners and control the blockchain. However if a miner (or a group of miners) have more than 51% of the hash power of the network, they essentially control what goes into the blockchain and the integrity is compromised. Also, the engergy consumption of PoW blockchains is extremely high.
Proof of Stake (PoS)
The concept of proof of stake is very similar to share holder voting in any company. Who ever owns the most stake (or the most coins) gets the privilege to mine the next block. Some blockchains also define stake in terms of the amount a time a person holds a coin (also referred to as the coin-age). Ethereum’s Casper Protocol is a Proof of Stake Protocol.
A 51% attack is generally considered more expensive in case of a proof of stake chain. However, many people are opposed to it ideologically as the it gives the ‘rich’ control over the blockchain. Also, there is a problem of ‘nothing-at-stake’ where a malicious miner looses nothing by betting on two different forks of the chain.
Delegated Proof of Stake (dPoS)
In delegated proof of stake, the stake-holders elect a delegate by means of a weighted election (the weights are proportional to their stake in the network). This delegate verifies the transactions, makes a block and receives a block for that.
This system is usually considered to be one of the fasted consensus algorithm that can scale up-to millions of transactions per second and is used by the EOS blockchain.
Delegated Byzantine Fault Tolerance (dBFT)
This consensus mechanism was made popular by the cryptocurrency NEO. This system is very
similar to a democratic system. Anyone who holds the cryptocurrency becomes a citizen. To
become a delegate the node needs to satisfy certain requirements like a good internet connection, specific equipment, etc. The citizens vote for delegates. One of the delegates is randomly chosen as the speaker. The speaker then proposes a new block which is verified by the other delegates. If 66% of the delegates accept the block, it is included in the blockchain. Otherwise another delegate is chosen as the speaker and the process is repeated.
There are also other consensus algorithms like Proof of Importance, Proof of Burn, Proof of
Activity, etc. It is an active area of research and new variants keep coming up with new blockchains.
Blockchain Evolution over time
Blockchain 1.0
It all started with Bitcoin, and quickly spread to other crypto-currencies as well. All the first
generation blockchains were created in an attempt to create a decentralised digital payment system and for this different crypto-currencies were made on models similar to Bitcoin.
Blockchain 2.0
This generation started with Vitalik Buterin and his vision for Ethereum to run smart contracts
which are essentially small programs that are present on the blockchain. Since they are on the blockchain, they become tamper-resistant.
Blockchain 3.0
This generation further extended the ideas of the previous generation with the introduction of
decentralised applications (or dApps). These are full fledged applications with a front-end and
back-end, however the back-end of these applications usually resides on a blockchain. This generation also introduced permissioned blockchains which place restrictions on who can join the network, who can mine the new blocks, etc. One of the most prominent blockchain in this generation is IBM Hyperledger.
Types of Blockchains
There are three main types of blockchains –
Public Blockchain
In a public blockchain, anyone can join the network, transact, and become a miner. Also, anyone can see and parse the contents of such blockchains. Bitcoin and Ethereum are popular examples of this category.
Private Blockchain
It is an invite-only blockchain. It is usually hosted on private networks by enterprises who do
not wish anyone to view or modify the data on the blockchain. Unlike public blockchains, it is
usually centralised however the data is still cryptographically secured from the company’s view point. Multichain is an example of a private blockchain.
Federated or Consortium Blockchain
It is mainly used by banks. In this the consensus is controlled by a pre-determined set of nodes. The right to read the blockchain may be restricted or open. Corda is an example in this category.
Blockchain Applications
Blockchain systems provide attractive properties like immutability, consensus, trust in a trust-less world, decentralisation, etc. These coupled with the fact the developers can write small programs called Smart Contracts that reside on the chain has made way for a whole new area of software development and research called decentralized applications (or dApps). They are applications that leverage the properties of a blockchain system to give solutions for real world problems. Finding new areas for blockchains and distributed ledger technology is an active area of research. Money transactions is an obvious application for all the cryptocurrency backed blockchain platforms. Blockchains have been used for e-governance, digital identity management, land record registry, etc. Supply chain and proof of provenance is also an active area of research.
Ethereum Primer
Introduction to Ethereum
Ethereum is also a cryptocurrency backed blockchain like Bitcoin. It uses similar techniques like proof of work (it will eventually move to a proof of stake based consensus algorithm called Casper), hash pointers (Ethereum uses KECCAK-256), etc. However, the main difference between Ethereum and Bitcoin is that unlike Bitcoin which is just a distributed ledger of transactions, Ethereum can also run small computer programs which allow developers to develop decentralized applications (or dApps). Also, unlike Bitcoin whose founder(s) are unknown, Ethereum is the vision of Vitalik Buterin, who wrote the white paper . It is maintained by the Ethereum Foundation. Unlike Bitcoin, Ethereum has two kinds of addresses
- Externally Owned Accounts (EOAs) – these accounts are owned through public-private key pairs.
- Contract Accounts – these are special accounts which are controlled by the smart contract deployed on them. They can be triggered only by an EOA.
Like in Bitcoin, the users have to pay a small transaction fees for each transaction they want to
be entered on the blockchain. This is paid in Ethereum’s native currency called Ether.
Smart Contracts
Smart Contracts are essentially small programs that exist on the blockchain and are executed by the Ethereum Virtual Machine (EVM). They do not need any centralised trusted authority like banks since all the functionality required is implemented in the smart contract logic, and since the code itself resides on the blockchain we can be sure that it has not been tampered with. This property of being immutable is crucial in financial applications like escrow and other payments. Also, it allows developers to develop other smart applications by utilizing the power of blockchain technology.
However, the concept of smart contracts is not new. It was introduced by Nick Szabo in 1997.
EVM
EVM stands for Ethereum Virtual Machine which serves a similar purpose that Java Virtual
Machine (JVM) does for Java by providing a layer of abstraction between the code and the machine. This also makes the code portable across machines. It also gives the developers an option to code in their smart contract language of choice, as finally all the programs written in different languages are translated by their respective compilers to EVM byte-code. The Ethereum Yellow Paper explains the intricate workings of the Ethereum Virtual Machine in great detail. The EVM has 140 opcodes which allow it to be Turing complete. Each opcode
takes 1 byte of storage space. The EVM also uses a 256 bit register stack which holds 1024 items. It also has a contract memory for complicated operations but it is non persistent. For storing data indefinitely, storage is used. Reading from storage is free, but writing to storage is extremely expensive.
Smart Contract Programming
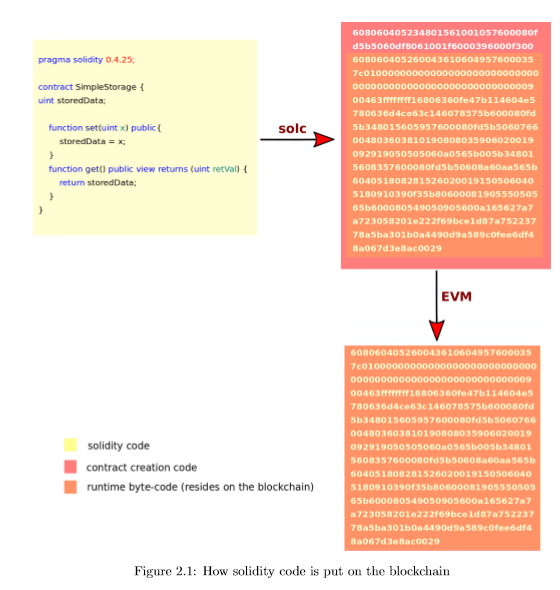
The most popular programming language for Ethereum Smart Contracts is Solidity. It is a language similar to Javascript and C++, making it easy for existing software developers to write solidity code. Other languages, though not as popular are Vyper and Bamboo. Before Solidity was released, languages like Serpent and Mutan were used which have since been deprecated. The compiler (solidity’s compiler is called solc) converts the source code to EVM bytecode. This code is called the contract creation code. This is like a constructor to put the contract bytecode on the blockchain and can be executed by the EVM only once to put the run-time bytecode on the chain. The run-time bytecode is the code that is executed by the EVM on every call the contract. The run-time bytecode also contains a swarm hash of the metadata file. This file can contain information like functions, compiler version, etc. However, this is still an experimental feature and not many have uploaded the metadata to the Swarm network. Figure 2.1 explains this process graphically.
Ether and Gas
Ether is the native cryptocurrency of the Ethereum network. Gas is another feature of Ethereum that separates it from Bitcoin. Since different smart contracts require varying amounts of computational power and time, it would be unfair to the miners to base the transaction fees just on the length of the transaction or have a constant transaction fees. Gas is a unit introduced by Ethereum that measures the computational work done. Each operation
has an associated gas cost. However, gas is different from Ether as the value of the latter is market dependent but that does not change the ‘computational power’ required to execute the contract. Therefore, every transaction mentions a gas price which is the price a person is willing to pay in ether per unit of gas. The combination of these two give the transaction fees in ether. The concept of gas introduces two new scenarios –
- Transaction running out of gas – if the gas costs go beyond the value allotted, the transaction is marked as failed and is included in the blockchain. This also prevents miners getting stuck in infinite loop computations.
- Gas price too low/high – if the gas price is too low, no miner will pick up the transaction. On the other hand, if it is too high then it will become very expensive for the sender of the transaction.
Existing Related Work
• Atzei et. al. conducted the first survey of attacks on Ethereum smart contracts and also gave the first taxonomy of Ethereum smart contract vulnerabilities. They also look at some of the popular vulnerable contracts like the DAO, Rubixi, GovernMental and King of the Ether throne.
• Dika in his master’s thesis, extended the taxonomy given by Atzei et. al. . He also tested the effectiveness of three security tools on a data-set of 23 vulnerable and 21 safe contracts. It is observed that the data-set and the number of tools used for the study is quite less. Also, the taxonomy needs hierarchy for better analysis.
• Mense et. al. look at the security analysis tools available for Ethereum smart contracts and cross reference them to the extended taxonomy given by Dika to identify the vulnerabilities captured by each tool. However, the tool’s effectiveness in catching those vulnerabilities is not studied.
• Buterin in his post outlines the various vulnerable smart contracts with an elementary categorization. He also emphasises the need to experiment with various tools and standard
ization wherever possible to mitigate bugs in smart contracts.
• Angelo et. al. surveyed the various tools available to Ethereum smart contract developers. They do a very broad categorization of tools – those which are publicly available and
those which are not publicly available.
• Antonopoulos et. al. in their book on Ethereum have dedicated a chapter on smart contract security. They cover the various vulnerabilities encountered by smart contract developers and give real world examples and preventative techniques. It is a good reference for smart contract developers.
This article has been published from the source link without modifications to the text. Only the text has been changed.
[ad_2]
Source link